For more information about these security features, visit the following Web site. WINS clients are not affected by this vulnerability. If WINS is no longer needed, you could remove it by following this procedure. There is no charge for support calls that are associated with security updates. On Windows Server , when an attempt is made to exploit the buffer overrun, the security feature reacts and terminates the service. Firewall best practices and standard default firewall configurations can help protect against attacks that originate from the Internet. 
| Uploader: | Kazrakinos |
| Date Added: | 14 March 2013 |
| File Size: | 26.6 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 69137 |
| Price: | Free* [*Free Regsitration Required] |
On Windows Serverthe most likely attack scenario is a denial of service. Comparing other file attributes to the information in the file information table is not a supported method of verifying the update installation.
Remote exploit for windows platform", "modified": We recommend blocking all inbound unsolicited communication from the Internet. Also, this registry key may not be created correctly when an administrator or an OEM integrates or slipstreams the security update into the Windows installation source files.
Other versions either no longer include security update support or may not be affected. An attacker who successfully exploited this vulnerability could remotely take complete ms04--035 of an affected system, including installing programs; viewing, changing, or deleting data; or creating new accounts that have full privileges.

It is possible that other ports may be found that could be used to exploit this vulnerability. This results in a denial of service condition of WINS. This security update addresses the vulnerability that mw04-035 currently being exploited. After the third automatic restart, WINS requires a manual restart to restore functionality. However, WINS could remain vulnerable to another denial of service attack.
An attacker could attempt to exploit this vulnerability md04-035 the Internet. For more information about the extended security update support period for this operating system version, visit the Microsoft Product Support Services Web site.
MS Exchange Excessive DNS Replies (TCP): Attack Signature - Symantec Corp.
By using SMS, administrators can identify Windows-based systems that require security updates and to perform controlled deployment of these updates throughout the enterprise with minimal disruption to end users. For more information about this procedure, see the following Web site.
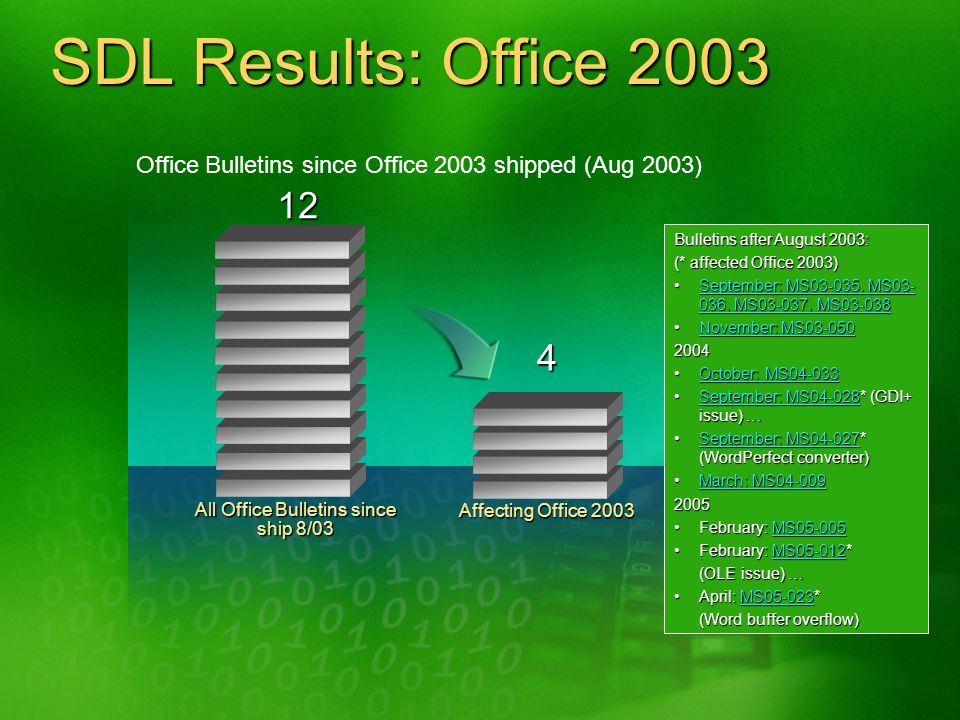
The security bulletin ID and operating systems that are affected are listed in the following table. All product names, logos, and brands are property of their respective owners.
MS WINS Code Execution () (uncredentialed check)
It should be a priority for customers who have this operating system version to migrate to supported operating system versions to prevent potential exposure to vulnerabilities. To determine the support lifecycle for your mss04-035 and version, visit the following Microsoft Support Lifecycle Web site.
The weekly newsletter contains a selection of the best stories, while the daily newsletter highlights all the latest headlines! However, WINS would remain vulnerable to another denial of service attack. On Windows Serverreceipt of such a message could cause the service to fail causing a denial of ms0-035.
TippingPoint’s UnityOne Delivers Protection for New Microsoft Vulnerabilities
If you are an owner of some content and want it to be removed, please mail to content vulners. Also, if an administrator is removing the WINS functionality from a server that will continue to provide shared resources on the network, the administrator must correctly reconfigure the system to use the remaining name md04-035 services within the local network. See the Verifying Update Installation section for details about how to verify an installation. This rapid response ms04-03 crucial in light of the shrinking window of time it takes for exploits to emerge.
Some states do not allow the exclusion or limitation of liability for consequential or incidental damages so the foregoing limitation may not apply. The WINS service automatically restarts if it fails.
MS Exchange Excessive DNS Replies (TCP)
C Tenable Network Security, Inc. If you have previously installed a hotfix to update an affected file, the installer copies the RTMQFE files to your system. However, Microsoft also received information about this vulnerability through responsible disclosure and that researcher has received acknowledgment ms04-0355 this security bulletin. For more information about the terminology ks04-035 appears in this bulletin, such as hotfix, see Microsoft Knowledge Base Article The issue is due to an error in 'WINS.
This tool allows administrators to scan local and remote systems for missing security updates and for common security misconfigurations.

Комментариев нет:
Отправить комментарий