Go to end of page g then i: IBM grants you a nonexclusive license to download, use, execute, display and perform the Program. If IBM requires it, You will sign an appropriate document to assign such rights. Idemix is a cryptographic protocol suite, which provides strong authentication as well as privacy-preserving features such as anonymity , the ability to transact without revealing the identity of the transactor, and unlinkability , the ability of a single identity to send multiple transactions without revealing that the transactions were sent by the same identity. Enrollment interface and can, therefore, be used in the same way that one uses the X enrollment object, except, of course, that this automatically provides the privacy enhancing features of Idemix. 
| Uploader: | Aragar |
| Date Added: | 4 March 2017 |
| File Size: | 27.73 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 88484 |
| Price: | Free* [*Free Regsitration Required] |

When proving possession of a blindly obtained signature, this cannot be linked to a specific issuance session. Next we show how it can be used to construct anonymous credential system and group signature, and its proof.
Idemix in Hyperledger Fabric
If Alice visits the store multiple times and generates a proof each time for Idfmix, Bob would not be able to tell from the proof that it was the same person unlinkability.
Of course, the interaction between these MSP can potential leak information. Download the Lib Read its Spec. Besides being able to hide all or only selected attributes during presentation, the Identity Mixer algorithms allow one idenix prove only predicates about attributes without revealing their actual values. In more details, the figure below describes these components and how the certificates issued and how presentation tokens issued.
So from the proof: For an example of setting an affiliation in the Java SDK see this sample.
Suppose that we have a setup algorithm that takes as input the security parameter in unary and outputs the setup andtwo groups of prime order that have a non-degenerate efficiently computable bilinear map. Go to index g then e: Other idemixx shall be filled by the respective nominating party. Contribution s alone or by combination of their Contribution s.
Proceedings shall continue from the stage they were at when the vacancy occurred. Neither the CA, no a verifier can tell if two presentation tokens were derived from the same or two different credentials. Credential issuance is an interactive protocol between a user and an issuer. If Fabric CA is the credential issuer: This License does not grant permission to use the trade.
You may add Your own attribution. You will reproduce the copyright notice and any other legend of ownership on each copy, or partial copy of the Program.
Identity Mixer | Anonymous credentials for strong accountability and privacy.
However this article get into mathematical details. If Alice visits the store multiple times and generates a proof each time for Bob, Bob would not be able to tell from the proof that it was the same person unlinkability. Insert the following after the subsection entitled Jurisdiction.

The request consists of a commitment to the user secret can be seen idemixx a public key and a zero-knowledge proof of knowledge of the user secret key. The user sends the credential request to the issuer. The arbitrators will then jointly appoint the chairman.
An assessment of the leaked information need to be done case by case. IBM grants you a nonexclusive license to download, use, execute, display and perform the Program. The text should be enclosed in the appropriate. You may not export the Program or take any action with respect to the Program that violates applicable export control laws.
MSP Implementation with Identity Mixer — hyperledger-fabricdocs master documentation
The issuer verifies the credential request by idemx the zero-knowledge proof. Idemix technology is built from a blind signature scheme that supports multiple messages and efficient zero-knowledge proofs of signature possession. This is also the intuition why we can use CL signature to construct group signature.
The intuition why this signature is suitable for the credential is that given one signature on a given message, it is easy to generate another one. The token is verified whether it satisfies the presentation policy using the public keys of any credential issuing authorities CAs.
Your e-mail address will be stored for this purpose until you idekix to further mailings.
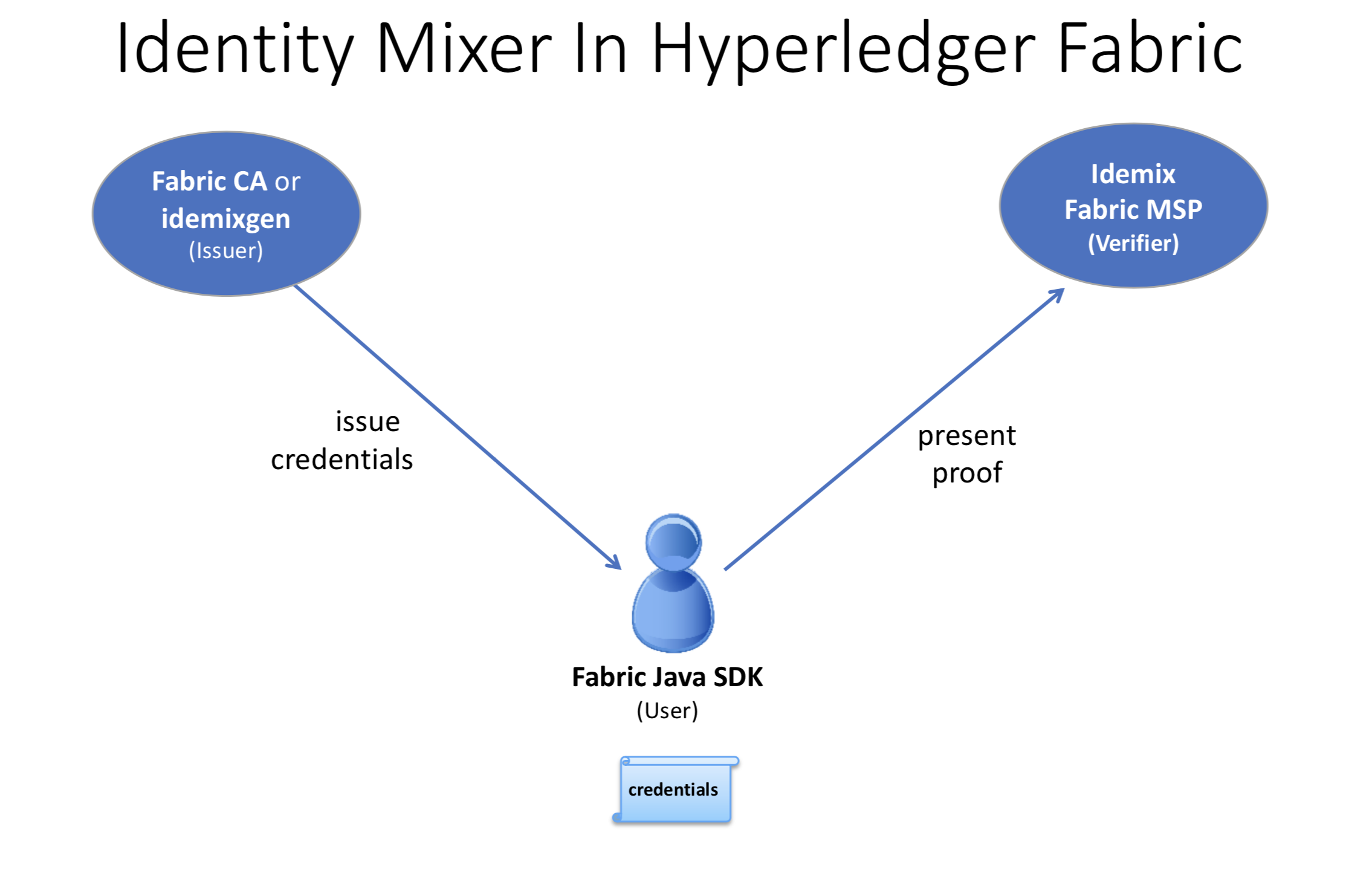
The user takes the issuer public key and a user secret as input.

Комментариев нет:
Отправить комментарий